Fixing exhaustive-deps warning in some common use cases
Let’s look at how we can adapt the right mental model of useEffect to fix the exhaustive-deps warning.…
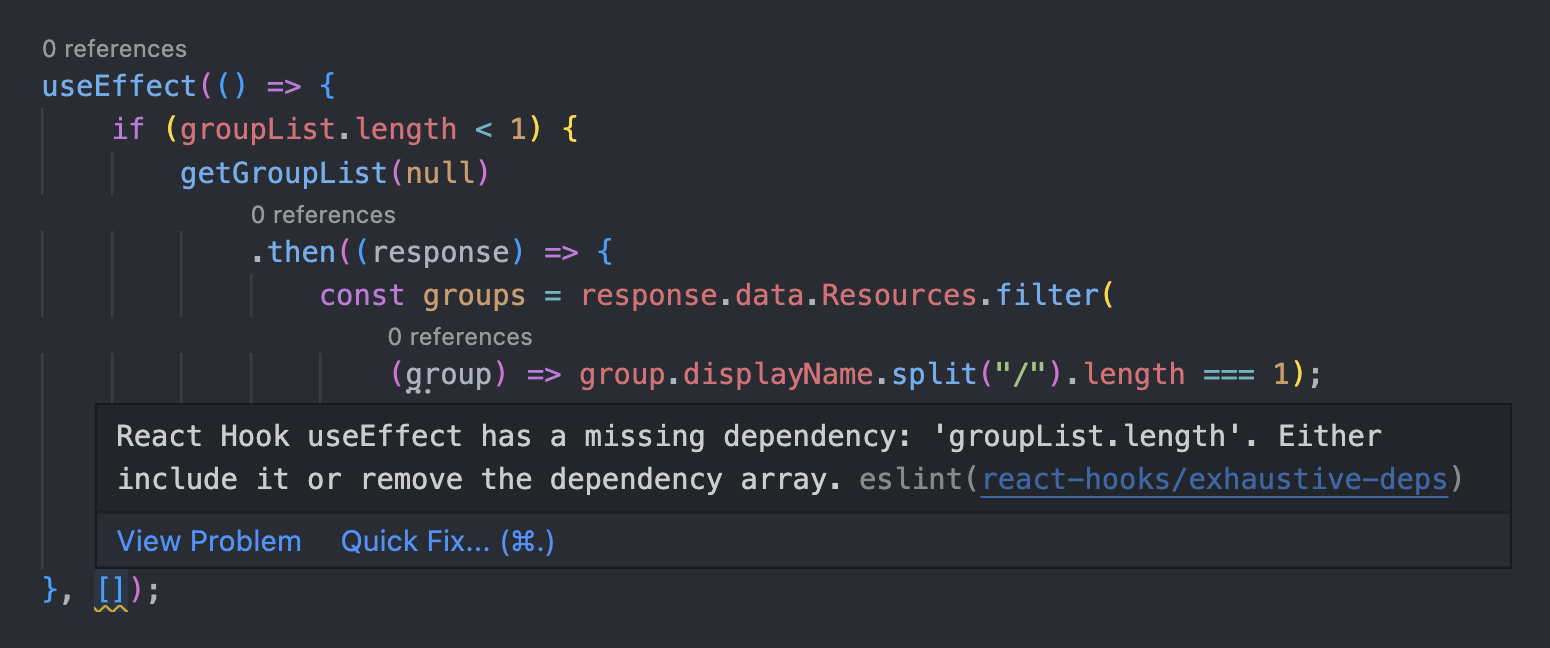
Let’s look at how we can adapt the right mental model of useEffect to fix the exhaustive-deps warning.…

I had a tryst with the eslint exhaustive-deps rule recently. It made me go down the rabbit hole and realize that I have been using the useEffect hook wrong. In this article, I will be…

useTransition and useDeferredValue are two new hooks React introduced with React 18 earlier this year. These two hooks make use of React’s concurrent rendering to allow developers to provide a better user experience in their…

Passwords are becoming obsolete, and the tech world is exploring various different technologies to allow users to log in without passwords. In this article, we discussed the perils of passwords and how FIDO2 can help us go…
In the previous article, we looked at the motivation behind blockchain. In this article, let’s look at the challenges of a decentralized digital financial transaction system. As we saw in the previous article, in a…

The online literature on blockchain is torn between too simplistic rundowns for non-techies and advanced hieroglyphic riddles targeted at those who want to learn blockchain in depth. When I started learning blockchain, unfortunately, hardly did…
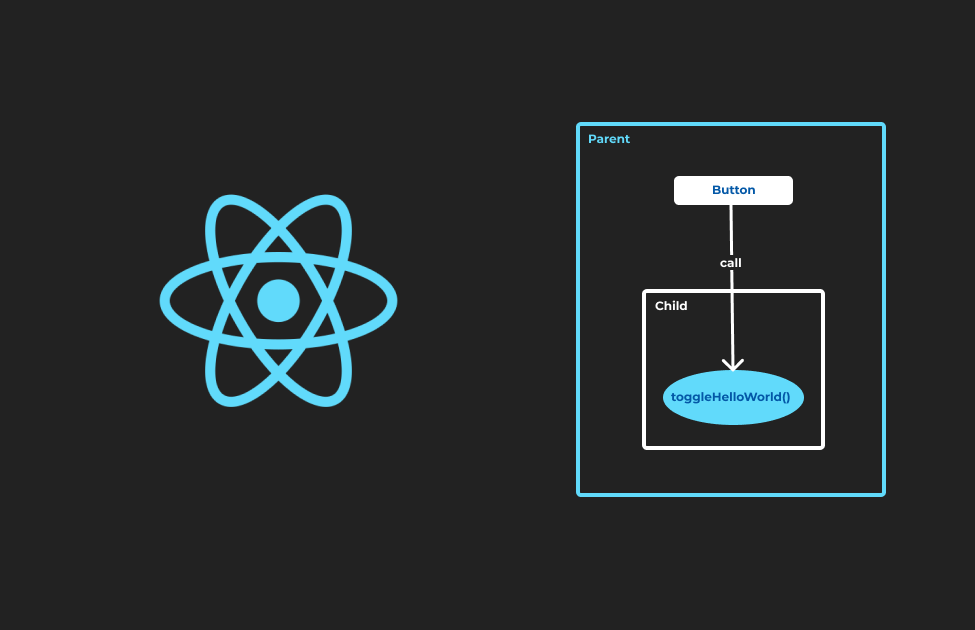
Invoking a parent component’s method from a child component is pretty straightforward in React. We can do it by passing the method as a prop to the child component. But what if we want to…

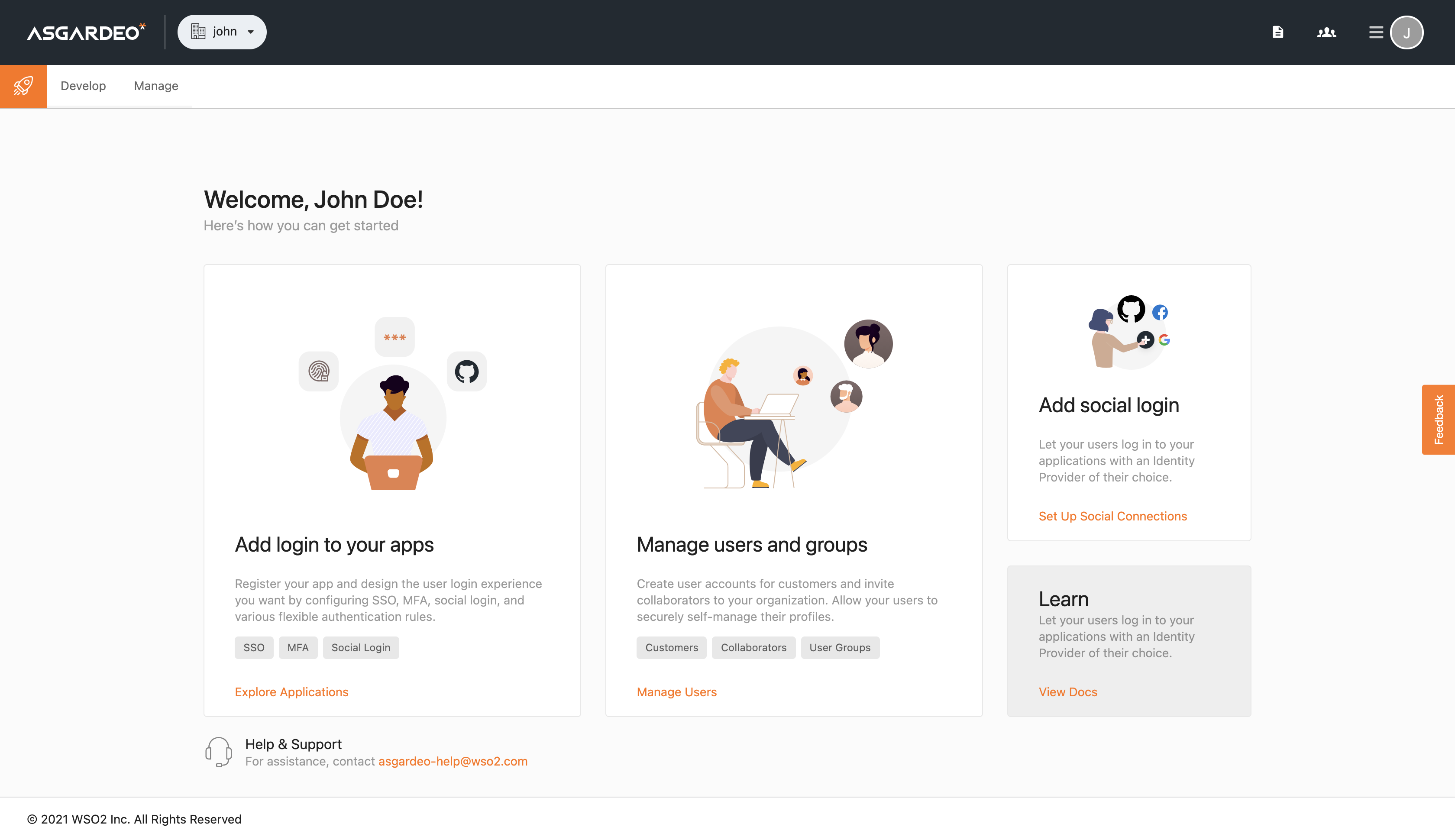
Passwords are fast becoming a thing of the past and for the right reasons. For better user experience and security, services should allow their users to log in without passwords. With Asgardeo, this should be…

Wordle is intriguing, I know. But what was more intriguing to me was how this web app worked. So, I decided to peek through the code, and eventually, I decided to build a Twitter bot…

Very often, we need to protect APIs and a very good way of doing it is to use Open ID Connect (OIDC) authentication. In this article, we are going to take a look at how…

Browser redirection is an integral part of the Open ID Connect (OIDC) authentication flow. At the same time, it is every UX engineer’s nightmare. Of course, we can do nothing to carry out OIDC authentication…

Do you want to add authentication to your Angular app? Gone are the days when you had to implement the backend logic to manage users and then write the frontend logic to manage user sessions.…
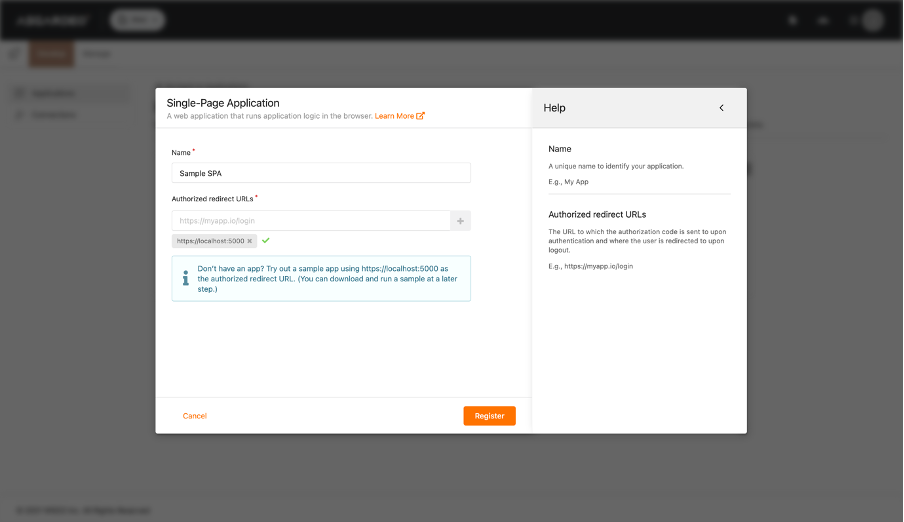
More often than not, securing access to your Single-Page Application (SPA) inevitably becomes an integral part of development. Asgardeo simplifies this by providing you with an Identity and Access Management (IAM) solution coupled with a…

Single-Page Applications (SPAs) are fast becoming ubiquitous as they provide a far better user experience over the traditional multi-page applications. However, as is often the case with app development, a good user experience and security…
Times change fast. Even more so if you are in the tech business. Fifteen years ago, JavaScript was only a child’s toy condemned to lend some semblance of programmability to web pages. Today, it is…

Implementing a timer using React might seem straightforward until you actually try to implement one. This seemingly run-of-the-mill task can put your React knowledge to a stern test. The obvious way First, let us try…